Featured
Introduction Misconfigurations in cloud environments and resulting data breaches frequently put AWS Simple Storage Service in the news. In “Hands-On AWS Penetration Testing with Kali...
Red Team
Introduction Today’s businesses depend more heavily than ever on applications and data analytics. The more an organization transitions its processes to digital systems, the more data it can take...
Introduction ISO 27001 compliance entails proving that an organization’s information security management system (ISMS) aligns with the standard’s requirements. Achieving compliance...
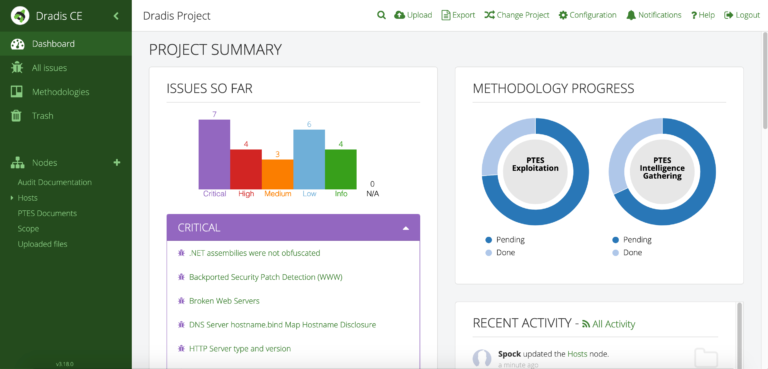
Introduction As cyber security professionals traverse the complex landscape of security assessments and penetration tests, smooth reporting and collaboration are critical for success. One tool that...
Introduction In many cases, penetration testing – an ethical engagement designed for identification and addressing of security vulnerabilities in systems, applications and networks, is required...
The British Library has released a report providing insights gained from the cyber incident that paralysed its IT systems in October last year. This occurred due to a terminal server implemented by a...
Blue Team
Zacks Investment Research Data, a major stock market data research provider, revealed a major breach in their network allowing attackers to expose 820,000 individual’s data. This data included names...
In May 2023, a managed file transfer program named MOVEit, used by a wide range of private businesses and government agencies experienced major data breach from an SQL injection attack on public...
TMX Finance, parent company of TitleMax, TitleBucks and InstaLoan experienced a major breach of their network, resulting in nearly 5 million customer accounts’ data being siphoned out by malicious...
23&Me, a California-based genetic testing company, experienced a major breach in early October 2023, of around 7 million customer records. Prior to the major breach, regulatory filing revealed...
Everyday and Travel
In today’s interconnected world, cyber security has become paramount. As our reliance on digital technology grows, so too do the threats posed by cyber criminals. From personal data breaches to...