
The Difference Between CTFs and AppSec
1. Real Applications Are Vastly More Complex CTFs typically involve hunting for vulnerabilities in custom-built applications designed specifically for the challenge. These apps are intentionally[…]

A Guide to AWS S3 Bucket Penetration Testing
Introduction Misconfigurations in cloud environments and resulting data breaches frequently put AWS Simple Storage Service in the news. In “Hands-On AWS Penetration Testing with Kali[…]

A Complete Guide To ISO 27001 Penetration Testing
Introduction ISO 27001 compliance entails proving that an organization’s information security management system (ISMS) aligns with the standard’s requirements. Achieving compliance requires undergoing an audit[…]
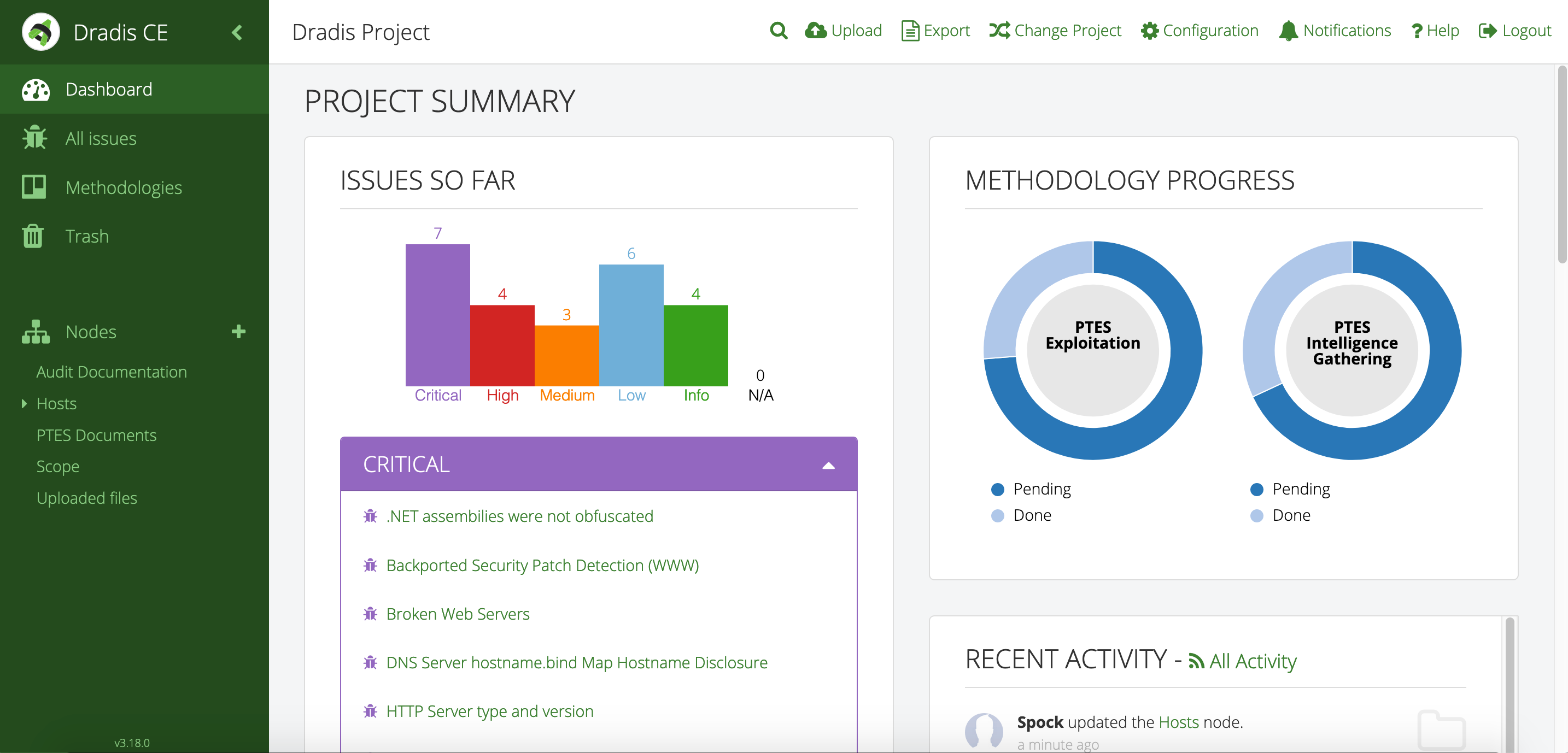
An Introduction to Report Generating With Dradis
Introduction As cyber security professionals traverse the complex landscape of security assessments and penetration tests, smooth reporting and collaboration are critical for success. One tool that has gained[…]

A Penetration Testing Compliance Guide
Introduction In many cases, penetration testing – an ethical engagement designed for identification and addressing of security vulnerabilities in systems, applications and networks, is required. Sometimes[…]

What We Know About the 2023 British Library Data Breach
The British Library has released a report providing insights gained from the cyber incident that paralysed its IT systems in October last year. This occurred[…]


