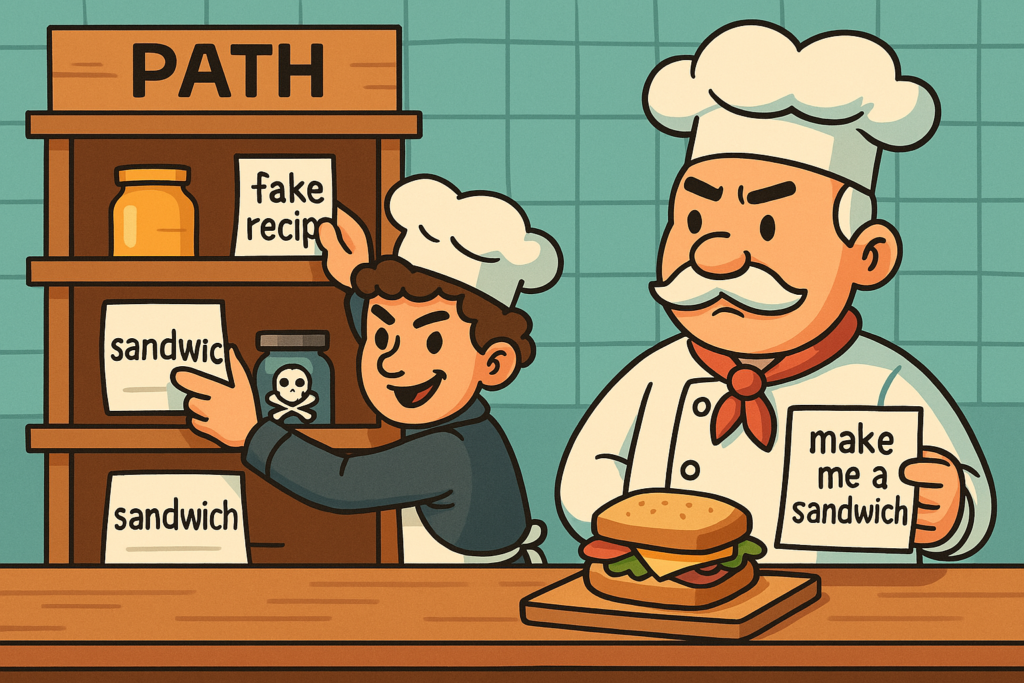
$PATH Exploitation ⬇️
Imagine your computer is a restaurant kitchen. In this kitchen, there’s a head chef (your system) who gets orders like “make me a sandwich” (run a command). But the chef doesn’t make the sandwich themselves. Instead, they look around the kitchen shelves (your system’s PATH) to find the right tool or recipe (i.e. the correct program or binary) to fulfil the order.
These shelves are searched in a specific order, one by one. As soon as the chef finds something labelled “sandwich” on a shelf, they use it, even if it’s not the real sandwich recipe, just something named the same.
The Attack Vector:
Let’s say you’re a mischievous kitchen helper (a low-privileged user). If you know the chef is going to ask for a “sandwich,” and you can sneak in your own fake recipe and put it on a shelf that the chef checks first, then your sandwich gets made, not the real one.
That’s PATH exploitation.
Technically speaking, when a script or a user with higher privileges runs a command without specifying the full path, the system searches for the binary using the $PATH environment variable.
If you, as a low-privileged attacker, can place a malicious binary or script with the same name as a commonly used command in a directory that appears earlier in PATH, and then trick the system (or a root user/SUID binary) into running it, your code executes instead of the legitimate one.